As artificial intelligence systems rapidly advance, the pace of change often outstrips the capabilities of traditional security programs. New models, an influx of tools, and evolving agent behaviors across various code bases present a pressing question: what constitutes an AI system, and how is it constructed?
The answer is found in Cisco’s AI BOM (AI Bill of Materials), now available with Cisco AI Defense and as an open-source utility. This tool provides security and engineering teams with a transparent inventory of AI components, along with the context necessary to comprehend how these elements function within an agentic workflow.
The AI Inventory Gap
While traditional Software Bill of Materials (SBOM) focuses on software packages and their dependencies, cloud visibility platforms offer insights into deployed cloud infrastructure that may encompass AI assets like models, MCP tools, agents, and prompts. However, this approach lacks the depth required for full visibility into AI systems. For instance, an AI chat application may interface with numerous agents, utilize various MCP tools, and incorporate other constructs and data storage solutions, such as vector databases, to generate coherent responses to user questions. Therefore, organizations need to deepen their understanding of AI-specific building blocks—models, agents, tools, prompts, and the workflows connecting them—by delving into the source code of AI applications, scanning code repositories or container images to craft a thorough AI BOM.
Without this comprehensive visibility, teams could encounter significant AI supply chain risks, including:
- Unauthorized or unexpected models being introduced into production
- Shadow tools or agent functionalities extending beyond their intended use
- AI workflows interacting with sensitive data lacking defined lineage
- Incomplete governance and auditing trails for AI systems
Cisco’s AI BOM: A Unique Approach
Cisco’s AI BOM is specifically designed to map the AI resources involved in AI applications. In its initial version, it scans code bases and container images to pinpoint AI elements such as agents, prompts, models, and tools, producing a structured report detailing how these AI assets interact. This foundational work enables more profound lineage and dependency analysis.
Three guiding principles shape the approach of Cisco’s AI BOM:
- AI Asset Discovery
This principle prioritizes the identification of AI assets pertinent to security and governance, as opposed to merely general dependencies. Traditional SBOMs have largely concentrated on software package dependencies. - A Curated Knowledge Base
Backed by a regularly updated knowledge database, it offers a comprehensive categorization of code constructs, covering over 10 popular AI and agentic frameworks, including Langchain, OpenAI, AWS BedRock, Autogen, Anthropic SDK, and Google GenAI, to name a few. This serves as crucial grounding information for mapping discovered AI assets in source code. - AI Asset Dependency Graph
The AI BOM generates dependency graphs that illustrate how AI assets are coordinated within an AI application, showcasing the relationships among agents, models, MCP tools, and prompts as revealed through code scans.
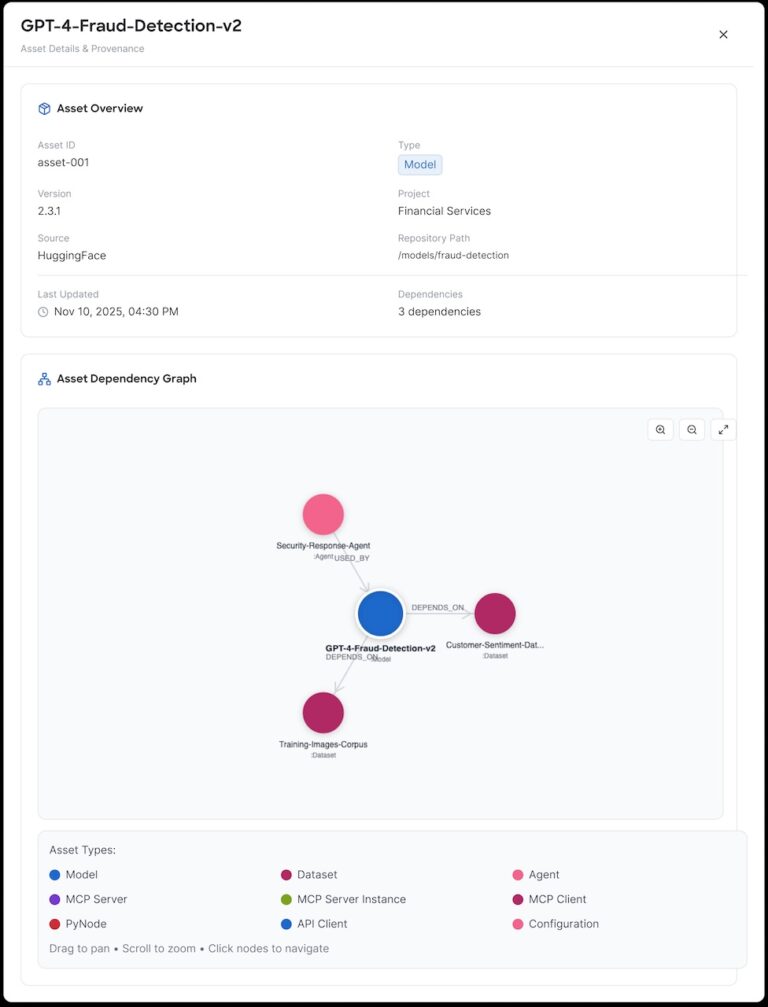

This unique combination makes the AI BOM actionable, clarifying what assets are present, how they are utilized within AI applications, and their positions in your AI ecosystem.
Cisco’s Strategy for AI Security
Cisco AI Defense enhances the security of the AI application lifecycle through a cohesive strategy encompassing Discovery, Detection, and Protection.
The security process begins with Discovery, which is aimed at identifying AI assets and understanding their uses. AI Defense offers visibility across AI models, agents, and associated data sources. The AI BOM complements this discovery process by revealing how AI applications are constructed from source code and container images, thus offering insights into AI assets like models, agents, MCP tools, and frameworks.
Detection leverages this asset visibility to identify potential risks even before they impact production. AI Defense scans files related to models, agents, prompts, and MCP tools to spot malicious or unsafe AI assets as part of a risk management strategy. Additionally, it employs algorithmic red teaming through AI Validation to uncover safety, security, and privacy vulnerabilities in AI assets and applications.
Protection addresses threats in real-time. By maintaining comprehensive visibility into AI assets, AI Defense Runtime can apply safeguards to production AI applications and agents, preventing harmful responses and attacks as they occur. Together, these capabilities facilitate the transition from sporadic audits to consistent, repeatable AI security practices throughout the AI application lifecycle.
Get Started
Cisco’s AI BOM is an open-source, command-line interface utility that is now available for early experimentation, enhancement, and integration into developer workflows. Discover the project, review its methodology, and engage with the community at the GitHub repository: https://github.com/cisco-ai-defense/aibom